disk mirroring (RAID 1)
What is disk mirroring (RAID 1)?
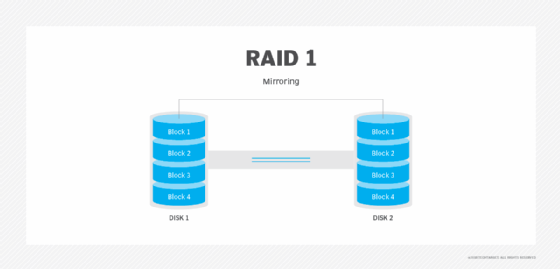
Disk mirroring, also known as RAID 1, is the replication of data across two or more disks. The term "disk mirroring" is sometimes used in a broader sense to describe any type of disk replication, but in most cases, it is meant within the context of RAID 1.
Disk mirroring ensures that there is at least one exact copy of the data at any given time in case of drive failure or other significant event. For this reason, a RAID 1 array requires a minimum of two physical drives, which is the typical configuration. It's possible to set up an array with three or more drives if the RAID controller supports it, but most IT teams opt for only two drives. If they want additional redundancy, they might back up the data to additional drives, rather than incorporating them into the RAID array.
The operating system sees the drives in a RAID 1 array as a single logical disk. The array's controller manages the disk array and its related functions and writes data to all the drives simultaneously. The drives are essentially mirror images of each other. If one drive fails, the controller automatically switches to the array's other drive, with minimal disruption to the workflow.
Disk mirroring can be used with both hard disk drives (HDDs) and solid-state drives (SSDs). Ideally, the drives used in a RAID 1 array are identical or as close to identical as possible. Using mismatched drives can result in wasted hardware resources. The array's capacity is limited to the smallest drive, and its write performance is only as good as the slowest drive.
What are the advantages and disadvantages of disk mirroring?
A RAID 1 array can operate with only one functioning drive. Because of this, disk mirroring can be used as part of a disaster recovery (DR) strategy for mission-critical applications. If the primary drive fails or is unavailable for any other reason, the RAID controller switches all traffic to the other drive, providing instantaneous failover to the mirrored copy.
The mirrored copy is immediately operational on failover. Because it contains an exact copy of all the data, it can seamlessly support the current workloads. The failed disk can then be replaced and the data copied over from the array's second drive. To support these types of operations, the controller might provide features such as disk hot-swapping or auto-rebuild.
Disk mirroring can also improve read operations for certain workloads because data can be read from multiple drives in parallel, assuming the drives are operational at the same time. However, writing to the drives can be slower because the data is written to multiple locations. Some RAID controllers have overcome this limitation and now provide write performance comparable to a single disk.
Even if write performance is not an issue, the DR capabilities inherent in disk mirroring come at a significant cost. Disk mirroring requires at least twice as much storage space as a single disk. For example, in a RAID 1 configuration with two 20 terabyte (TB) drives, half the capacity is needed for redundant data. This means that the array can store only 20 TB of data even though the drives have a combined capacity of 40 TB.
How does RAID 1 compare to other RAID levels?
RAID, which means "redundant array of independent disks" or "redundant array of inexpensive disks," is a method of grouping individual physical drives together to form a single logical drive called a RAID set. A RAID set can help improve performance, fault tolerance, or both.
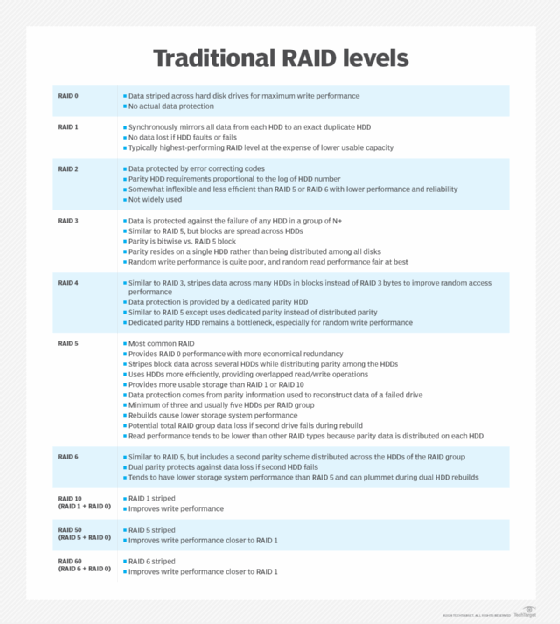
The way in which data is stored across an array's drives is called the RAID level. Each RAID level is denoted by a number following the word RAID. The most common levels are RAID 0, RAID 1, RAID 5 and RAID 6. The RAID level is typically selected to meet specific workload and data requirements. RAID 0 is the fastest, RAID 1 is the most reliable, and RAID 5 and RAID 6 provide a balance between the two.
RAID 1 (disk mirroring) is a good choice for applications that require high availability and good read performance, such as transactional applications, email servers and operating systems. However, it can also be expensive and potentially impact write performance. Although RAID 1 can improve read performance under certain circumstances, it's not the best RAID level for maximizing read performance.
Because of these limitations, few enterprise-class storage systems use RAID 1, opting instead for more space-conserving RAID 5 or RAID 6. In rare cases, IT teams will use RAID 0, although they're more likely to use RAID 10 (RAID 1+0), which combines RAID 1 and RAID 0. Here's a breakdown of how RAID 1 compares to these other RAID levels:
RAID 0. This RAID level uses striping to distribute data across multiple disks in the array. This approach optimizes both read and write operations, delivering better performance than disk mirroring. Unlike RAID 1, however, RAID 0 provides no data protection, so it should be used only for noncritical data.
RAID 5. This level uses striping like RAID 0, but it also stores parity information that can be used to reconstruct a disk in the event of failure. The use of parity data provides built-in redundancy, similar to RAID 1, but without requiring as much capacity. RAID 5 also offers read performance nearly comparable to RAID 0. However, RAID 5 cannot recover as quickly as a RAID 1 array. In many cases, RAID 1 can provide near instantaneous recovery, while RAID 5 needs time to rebuild the data across their arrays.
RAID 6. This level uses a construction similar to RAID 5, except that it adds additional parity data, making it possible to support two simultaneous disk failures. Beyond that, RAID 6 offers similar advantages and disadvantages as RAID 5, when compared to RAID 1.
RAID 10 (RAID 1 + 0). This type of RAID combines RAID 1 and RAID 0 to offer both performance and data protection. For example, an administrator can create two RAID 0 sets, and then combine the RAID 0 sets into a RAID 1 set. This essentially provides the performance benefits of RAID 0 with the availability benefits of RAID 1. Because RAID 10 uses mirroring like RAID 1, a good percentage of the available capacity is needed for redundant data. However, a RAID 1 array can contain as few as two drives, while RAID 10 requires at least four drives.
It is important to note that not all storage systems or RAID controllers support all the RAID levels. For example, a RAID controller might support only RAID 0 and RAID 1. Before purchasing a storage system or RAID controller, IT teams should determine the organization's specific needs relative to data protection and recovery and to application performance.
Learn about the key differences in software RAID vs. hardware RAID. Compare RAID levels 0, 1, 5, 6, 10 and 50 and read about the differences and benefits of RAID vs. backup.







